Whenever the Army creates a new Military Occupational Specialty (MOS), they have to fill it with bodies initially that aren’t actually the MOS. In late 2013 the Army graduated its first class of the new 25D Cyber Network Defender MOS. Shorty there after, the 25D, were placed into the unit COMSEC vaults to do a job that they were never designed to do.
Cyber Chief
Yes that’s right after over 19 years of wearing signal orange I have traded it in for cyber grey.
May Selection Board Results
This was a busy month with board results to post for both 170A, 255A, and 255N.
Happy Birth(day) CYBERCOM
Today marked several historic events for the Department of Defense. In the course of a couple of hours, three big events happened.
Birth of Spam
So this morning I was listening to the radio on the drive into work when the DJ made an interesting statement. Turns out….he was right. Today marks the 40th anniversary of the very first spam message.
Boss of the SOC
Back in November I had the chance to attend the Splunk .conf conference here in DC. One of the big after hours events of the conference is the Boss of the SOC (BOTS) competition that puts teams against each other to try and analyze a set of data to identify a variety of indicators of compromise from an incident. After a little bit of talking, Splunk decided to release the BOTS app as an open-source project.
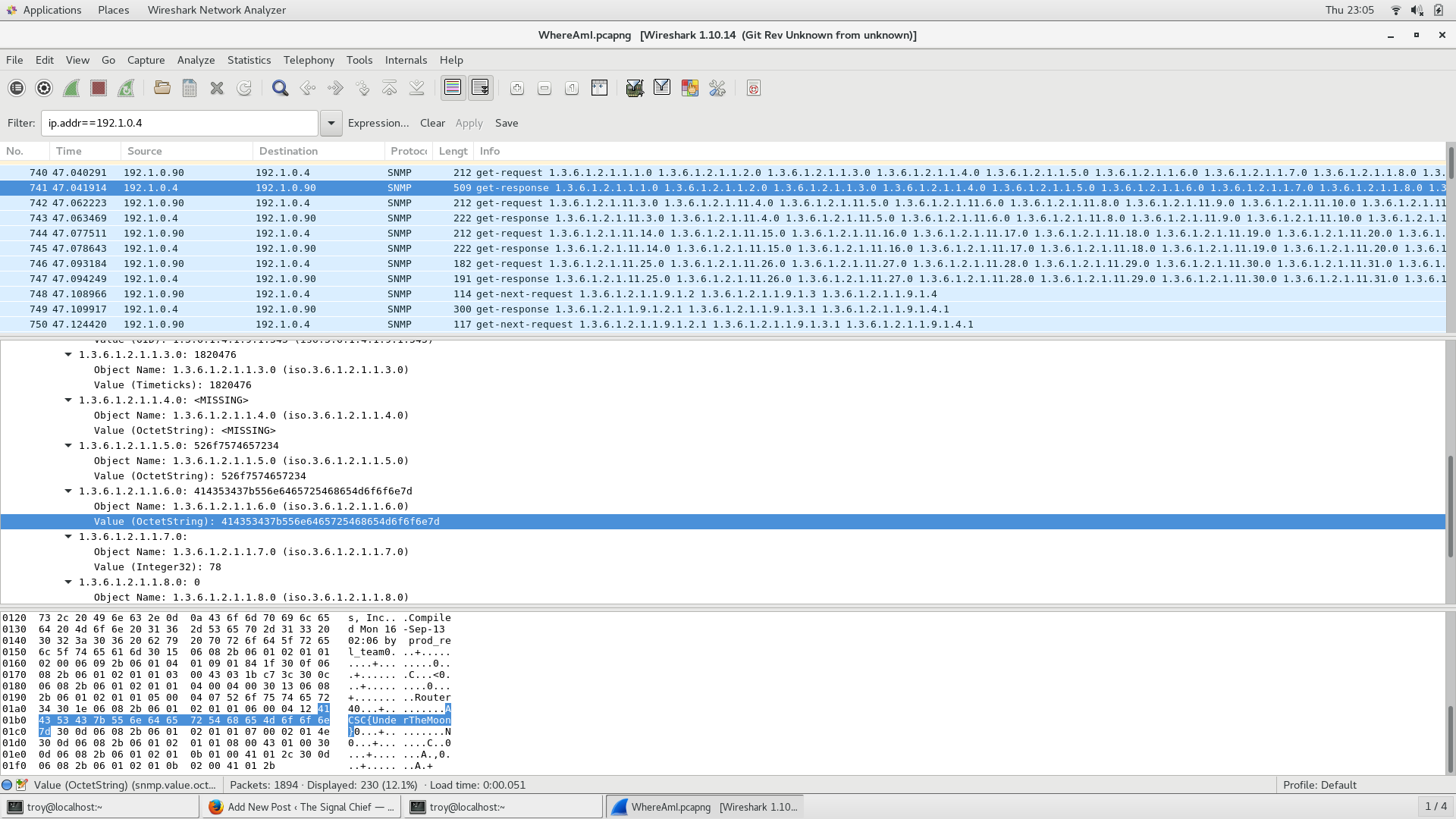
where_am_i
Another problem from ACSC5. You’ve been able to get on a router and capture some traffic in an effort to map out the the corporate network. Your intelligence team has told you that your target device has an IP address of 172.16.58.47 but no one knows that actual location of it. Examine the network traffic and see if you can figure out the location of that device.
Mandiant 2018 Trends Report
For anyone who doesn’t know, Mandiant is large cyber security company that was bought by Fireeye. They grabbed a lot of attention by the cyber security community when in 2013, they publicly released a report that linked the Chinese military to attacks dating back to at least 2006 on over 141 organizations. Each year they release a report on cyber security trends that they observed during the previous year. Granted, the results are screwed because they are based only on incidents that they responded to, but they at least give a good overall picture of what is going on around the world.
US and Russia Partner for Secure Elections
In what many analysts are calling a surprising move, Secretary of Homeland Security Kirstjen Nielsen on Friday announced that the department had completed a mutual assistance agreement with Russia to help ensure that each countries voting systems were secure.
Slow Mover
Another problem from the 5th annual Army Cyber Skills Challenge. The problem is called slow_mover and can be found here.
Problem
Your boss just handed you this PCAP that one of your network sensors captured. He’s positive that there is something fishy going on here but has no clue what it is.