For anyone who doesn’t know, Mandiant is large cyber security company that was bought by Fireeye. They grabbed a lot of attention by the cyber security community when in 2013, they publicly released a report that linked the Chinese military to attacks dating back to at least 2006 on over 141 organizations. This group became known at APT1 (This year’s report unveils APT35, a suspected Iranian group). Each year they release a report on cyber security trends that they observed during the previous year. Granted, the results are scewed because they are based only on incidents that they responded to, but they at least give a good overall picture of what is going on around the world.
 One of the things that I find most interesting about the report each year, is the amount of time between when an attack actually starts and when it is finally detected. Mandiant calls this dwell time, and it is the amount of time that the attacker has on the network to screw things up. This year, across the world, the average dwell time was 101 days. On the Americas continents, the average time was 75 days, while Europe, Middle East, and Africa (EMEA) was 175 days (up from 106 the year before) and in a very distant third place at 489 days (up from 172) was the Asia-Pacific (APAC) region. The worse part of this, is that APAC was home to the largest dwell time that they have observed of 2,085 days (about 5 years and 9 months). The good news is that the global average of 101 is well down from the first time they released numbers in 2011 which had an average of 416.
One of the things that I find most interesting about the report each year, is the amount of time between when an attack actually starts and when it is finally detected. Mandiant calls this dwell time, and it is the amount of time that the attacker has on the network to screw things up. This year, across the world, the average dwell time was 101 days. On the Americas continents, the average time was 75 days, while Europe, Middle East, and Africa (EMEA) was 175 days (up from 106 the year before) and in a very distant third place at 489 days (up from 172) was the Asia-Pacific (APAC) region. The worse part of this, is that APAC was home to the largest dwell time that they have observed of 2,085 days (about 5 years and 9 months). The good news is that the global average of 101 is well down from the first time they released numbers in 2011 which had an average of 416.
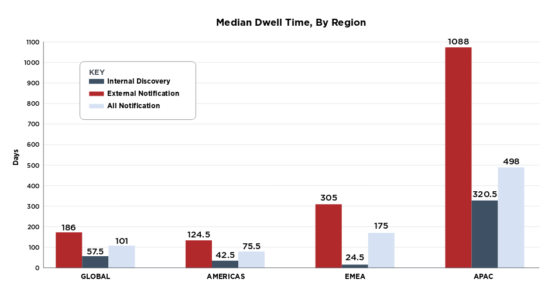
Within the dwell time numbers is a more interesting breakdown of how the companies found out. Generally you find out that you have been attacked one of two ways….you find it yourself, or someone else tells you. In the Amerias the average amount of time it took someone else to tell a company that they had been attacked was 124 days while companies that found it themselves found it in 42 days. This tells me that companies with a good internal cyber security team are much more likely to find an attack much quicker and significantly reduce the amount of damage that can be done. In EMEA outside notification took 305 days while internal notification only took 24 days. Finally for APAC outside notification took a whopping 1088 days while internal notification took a measly (relatively speaking) 320 days. Within this number it was also brought out that 62% of all incidents were detected by internal teams.
The full report can be found on Fireeye’s site here. I encourage you to take a few minutes and read it. It has a lot more information and some additional interesting facts that anyone even remotely related to cyber security should be aware of.

You mean skewed not screwed right?
Meh probably both